Fault-tolerant web application design refers to the practice of designing and building web applications that can continue to function even in the event of a failure or unexpected interruption. This can include hardware failures, network outages, or other types of system-wide issues. The goal of fault-tolerant design is to ensure that the web application can continue to operate and provide services to its users even in the face of unexpected or adverse conditions.
In the context of a cloud environment, Designing fault-tolerant web applications on an AWS cloud environment involves using various AWS services and features to build a web application that can continue to function even in the event of a failure or an unexpected interruption. This may include using services like Amazon Elastic Compute Cloud (EC2) Auto Scaling, Elastic Load Balancing, and Amazon Relational Database to create a highly available and fault-tolerant web application architecture.
A classic example of designing a highly resilient, scalable, and fault-tolerant architecture involves using Amazon EC2 Auto Scaling, which will automatically add or remove instances from your web application based on the current traffic, ensuring that your application can handle fluctuations in usage and prevent downtime. Additionally, using Elastic Load Balancing, you can distribute traffic across multiple instances of your web application so that if one instance fails, the others can continue to handle requests.
Another important aspect of fault tolerance on AWS is the use of multiple availability zones. By deploying your web application servers across multiple availability zones, you can ensure that if one zone goes down, your application will still be available in other zones. You can also use the Amazon Route 53 service to route traffic to healthy instances.
Fault tolerance is important for business operations and goals because it helps to ensure that the web application is available and reliable for users at all times. Downtime or service interruption can result in lost revenue, decreased productivity, and damage to a company’s reputation. By designing for fault-tolerance, businesses can minimize the risk of these negative impacts and ensure that their web application is always available to their customers. Additionally, it also can help to provide disaster recovery, so in case of a significant event, the business can recover quickly, and its operation can continue. Therefore, fault tolerance can help to ensure that the web application is able to meet the needs of its users and support the goals of the business. This project focuses on offering a step-by-step process for building a fault-tolerant Web application architecture on AWS using CloudFormation and the AWS CLI. The scripts are split into two sections: one for establishing the network infrastructure and the other for creating a computing architecture. Before we get started, let’s take a high-level look at Cloudformation.
AWS Cloud Formation
AWS CloudFormation is an AWS service that allows you to use code (in the form of templates) to provision and manage your infrastructure on the AWS platform. This is known as “Infrastructure as Code” (IAC). With CloudFormation, you can create templates in YAML or JSON that define the resources you want to create and how they should be configured. These templates can then be used to create, update, and delete your resources in a predictable and controlled manner. This allows you to automate the process of managing your infrastructure, making it easier to scale, update, and maintain your resources. CloudFormation also allows you to version control your templates, making it easier to roll back to a previous version of your infrastructure if needed. Additionally, CloudFormation enables you to use pre-built templates known as “CloudFormation Stacks” which can be shared across teams and organizations to speed up the development process and also to share best practices.
CloudFormation enables you to use code to manage your infrastructure, making it easier to automate and scale your resources. This allows you to reduce the time and effort required to manage your infrastructure, and to ensure that your resources are always in the desired state. This makes it a powerful tool for organizations that are looking to implement Infrastructure as Code practices in their AWS environments. The official AWS CloudFormation documentation can be found here
This project offers a step-by-step process for building a fault-tolerant Web application architecture on AWS using CloudFormation and the AWS CLI. The scripts are split into two sections: one for establishing the network infrastructure and the other for creating computing resources.
Prerequisites
AWS account with appropriate permissions to create and manage resources
Iam User with the appropriate Permissions and Programmatic Acess
AWS CLI installed and configured with access keys
AWS CloudFormation templates (Network and Compute)
The project files(Network and Compute CloudFormation templates ) are available in this GitHub Repository
File Structure Of The Github Repo
network-infrastructure.yaml: CloudFormation template for provisioning network infrastructurenetwork-parameters.json: A sample file containing the parameters for the network infrastructure CloudFormation templatecompute-infrastructure.yaml: CloudFormation template for provisioning compute infrastructurecompute-parameters.json: A sample file containing the parameters for the compute infrastructure CloudFormation templateAWS CLI commands.txt: A text file containing the AWS CLI commands for creating the stacks using the provided templates and parameters files
The Network infrastructure cloud foundation template creates a VPC with a pair of public and private subnets spread across two availability zones. It also creates an Internet Gateway and NAT Gateways for the private subnets, along with the necessary routing and networking configurations. The Template also includes parameters for customizing the IP ranges for the VPC and subnets, as well as an environment name for easy identification of resources
Description: >
Jules Network Infrastructure Template
This template deploys a VPC, with a pair of public and private subnets spread
across two Availabilty Zones. It deploys an Internet Gateway, with a default
route on the public subnets. It deploys a pair of NAT Gateways (one in each AZ),
and default routes for them in the private subnets.
Parameters:
VpcCIDR:
Type: AWS::EC2::VPC
Properties:
CidrBlock: !Ref VpcCIDR
EnableDnsHostnames: true
Tags:
- Key: Name
Value: !Ref EnvironmentName
InternetGateway:
Type: AWS::EC2::InternetGateway
Properties:
Tags:
- Key: Name
Value: !Ref EnvironmentName
InternetGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
InternetGatewayId: !Ref InternetGateway
VpcId: !Ref VPC
PublicSubnet1:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
AvailabilityZone: !Select [ 0, !GetAZs '' ]
CidrBlock: !Ref PublicSubnet1CIDR
MapPublicIpOnLaunch: true
Tags: - Key: Name
Value: !Sub ${EnvironmentName} Public Subnet (AZ1)
PublicSubnet2:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref VPC
AvailabilityZone: !Select [ 1, !GetAZs '' ]
CidrBlock: !Ref PublicSubnet2CIDR
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: !Sub ${EnvironmentName} Public Subnet (AZ2)
....................................................................
PS: The code we posted above is just a snippet of the entire cloud formation template, which is available Here
The Network template will provision the following resources:
VPC: A VPC with the specified CIDR rangeInternetGateway: An Internet GatewayInternetGatewayAttachment: Attaches the Internet Gateway to the VPCPublicSubnet1: A public subnet in the first Availability ZonePublicSubnet2: A public subnet in the second Availability ZonePrivateSubnet1: A private subnet in the first Availability ZonePrivateSubnet2: A private subnet in the second Availability ZoneNatGateway1EIP: Elastic IP for the first NAT GatewayNatGateway2EIP: Elastic IP for the second NAT GatewayNatGateway1: A NAT Gateway in the first Availability ZoneNatGateway2: A NAT Gateway in the second Availability ZonePublicRouteTable: A route table for the public subnetsPrivateRouteTable: A route table for the private subnetsRouteTableAssociation for both Private and Public Subnets
The compute cloud formation template deploys a load balancer and its dependencies to host the Jule-web application servers. The template also includes security groups, an autoscaling group with its required launch configuration, target groups, and an IAM role for the compute instances.
Description: >
Uviekugbere Theophilus, Jules Webapplication
This template deploys a loadbalancer and it's dependencies needed to host my WebApplication Udagram!.
The contains, security groups, autoscaling group with it's required Launchconconfiguration,
Targetgroups and IAM role for my compute instances
Parameters:
EnvironmentName:
Description: A name that will be prefixed to resource names to enable easy identification
LBSecGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: Allow http to our load balancer
VpcId:
Fn::ImportValue:
!Sub "${EnvironmentName}-VPCID"
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 80
ToPort: 80
CidrIp: 0.0.0.0/0
SecurityGroupEgress:
- IpProtocol: tcp
FromPort: 80
ToPort: 80
CidrIp: 0.0.0.0/0
WebServerSecGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: Allow http to our hosts and SSH from local only
VpcId:
Fn::ImportValue:
!Sub "${EnvironmentName}-VPCID"
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 80
ToPort: 80
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: 80
ToPort: 80
CidrIp: 0.0.0.0/0
SecurityGroupEgress:
- IpProtocol: tcp
FromPort: 0
ToPort: 65535
CidrIp: 0.0.0.0/0
WebAppLaunchConfig:
Type: AWS::AutoScaling::LaunchConfiguration
Properties:
UserData:
Fn::Base64: !Sub |
#!/bin/bash
sudo apt-get update -y
sudo apt-get install apache2 -y
sudo systemctl start apache2.service
cd /var/www/html
echo "It Works! Our Servers are UP " >index.html
ImageId: ami-0747bdcabd34c712a
The Compute template creates the following resources:
UdacityS3ReadOnlyEC2: An IAM role that allows read-only access to Amazon S3 and full access to Amazon SSM.
ProfileWithRolesForApp: An IAM instance profile that references the JulesS3ReadOnlyEC2 role.
LBSecGroup: A security group for the load balancer that allows incoming HTTP traffic.
WebServerSecGroup: A security group for the web servers that allow incoming HTTP traffic and all outgoing traffic.
WebAppLaunchConfig: A launch configuration for the web servers that includes user data to install Apache and display an “It Works! Our Servers are UP !” message.
WebAppGroup: An autoscaling group that uses the WebApp LaunchConfig and is associated with the target group.
WebAppLB: A load balancer that forwards incoming HTTP traffic to the web servers.
WebAppTargetGroup: A target group that the load balancer forwards traffic to.
Steps
To use the template, you must install and configure the AWS CLI with the appropriate credentials.
Clone the template from the GitHub repository to your local machine
Log in to the AWS Management Console, create an IAM user with Programmatic access, and then create the security credentials to configure the AWS CLI
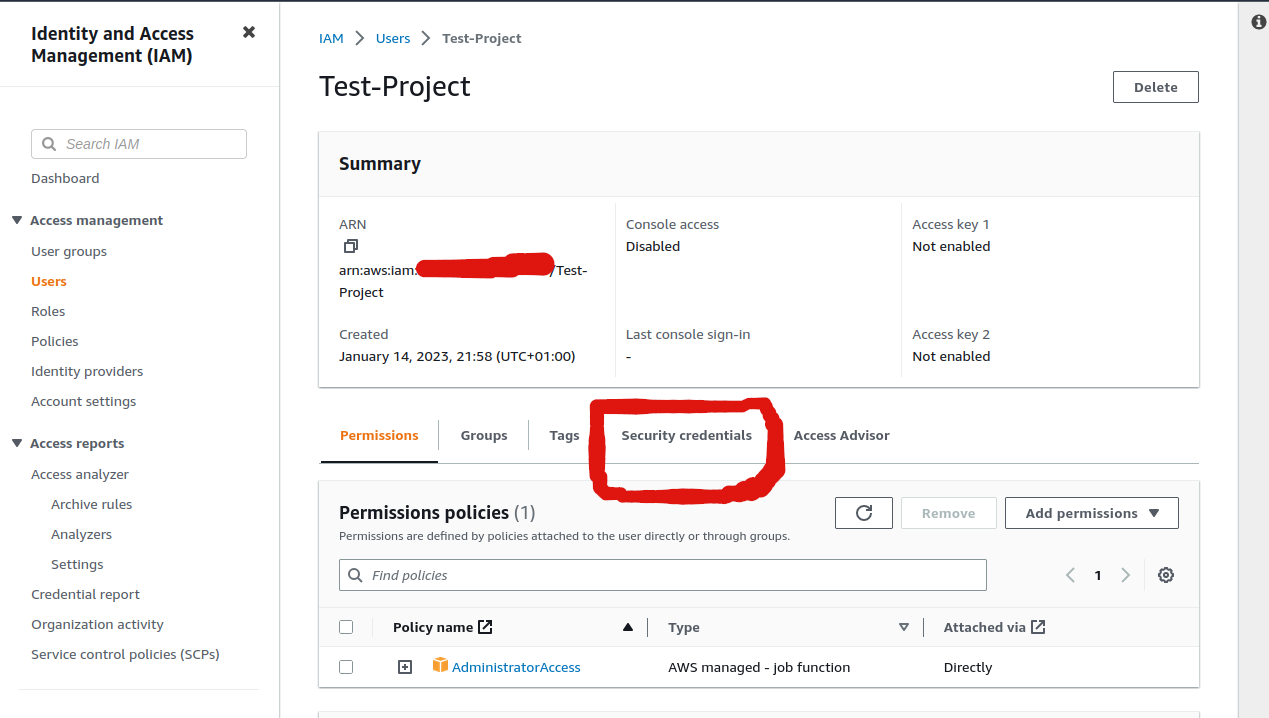
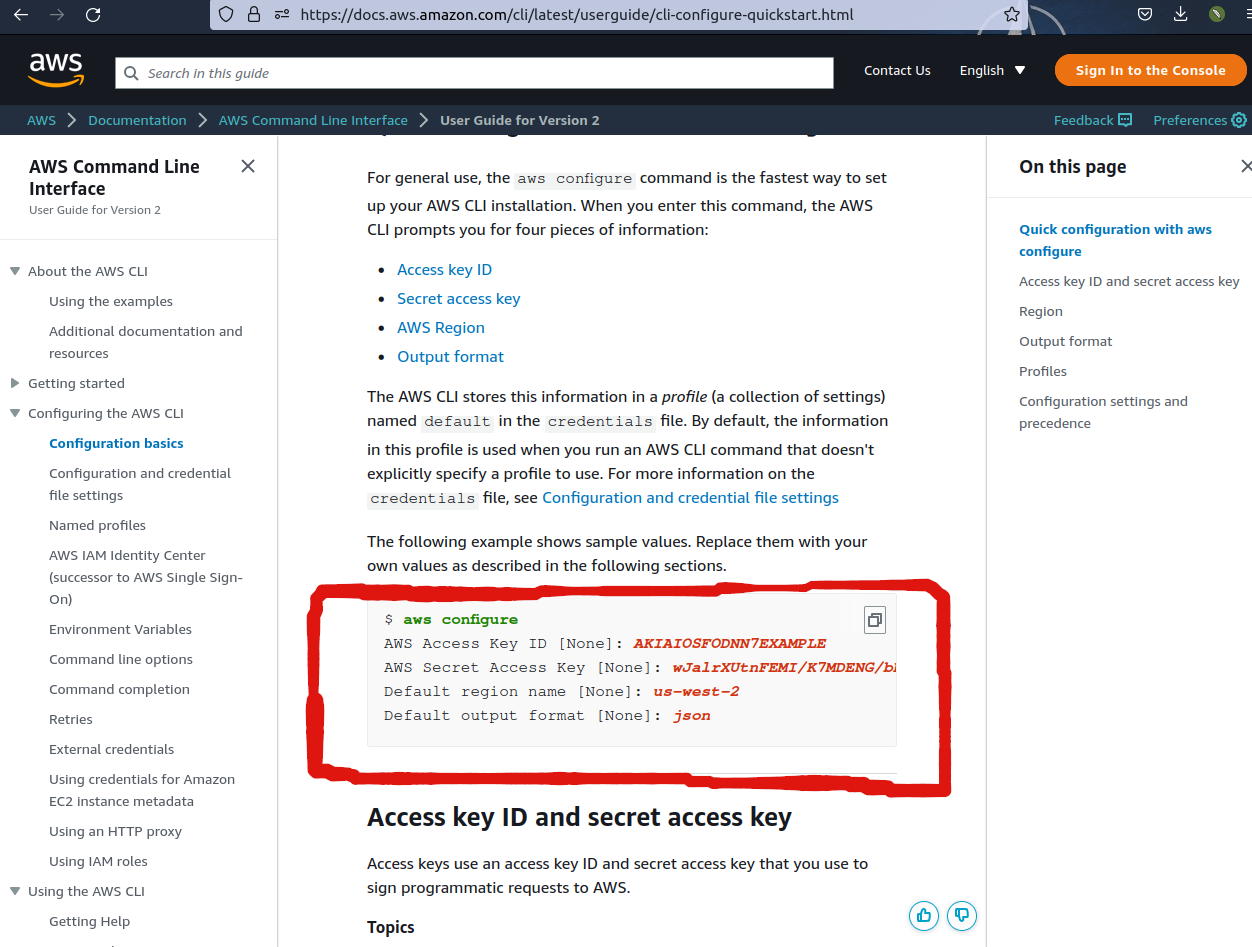
3. Configure the AWS CLI with the security credentials using the AWS CLI commands
aws configure
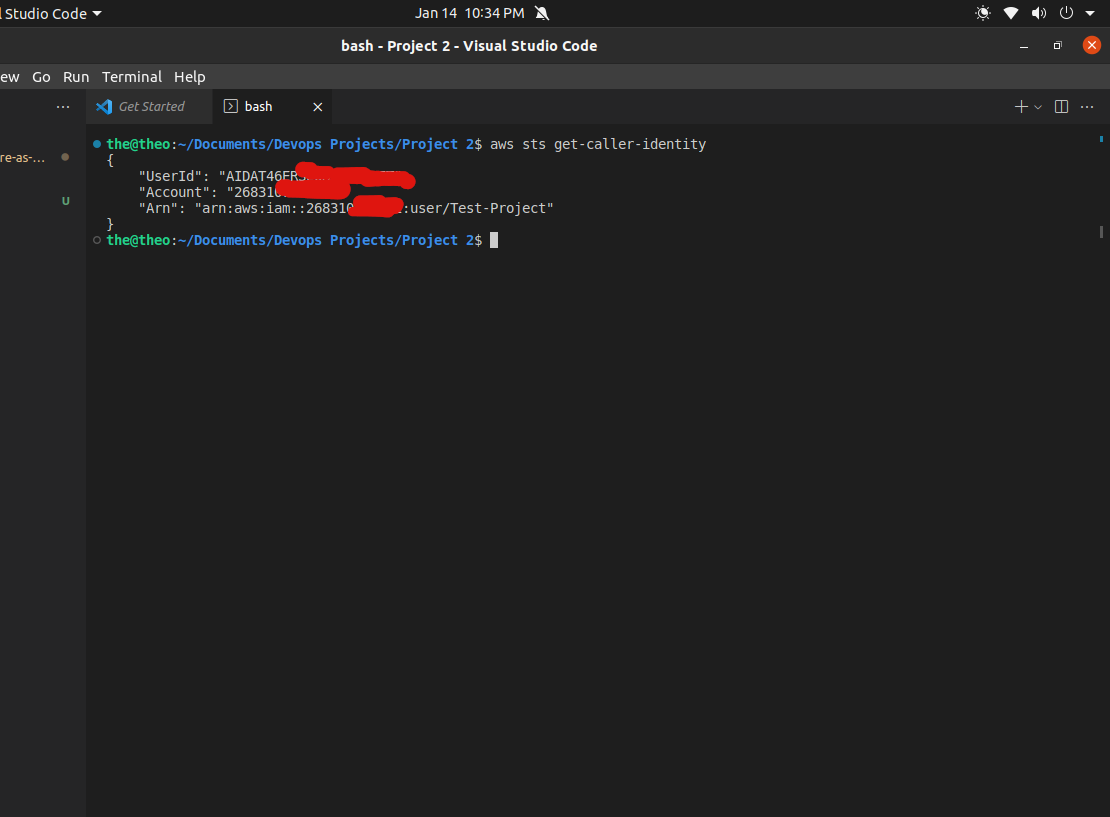
Then run the following command to check if the IAM user’s profile has been logged into the AWS CLI
aws sts get-caller-identity
4. Open AWS CLI commands.txt: A text file containing the AWS CLI commands for creating the stacks using the provided templates and parameters and running the commands.
FOR THE CREATION OF THE NETWORK INFRASTRUCTURE PLEASE RUN THIS AWS CLI COMMAND.
aws cloudformation create-stack --stack-name Network --template-body file://network.yml --parameters file://network-Parameters.json --capabilities "CAPABILITY_IAM" "CAPABILITY_NAMED_IAM" -- <region>
FOR THE CREATION OF THE COMPUTE RESOURCES PLEASE RUN THIS AWS CLI COMMAND.
aws cloudformation create-stack --stack-name Compute --template-body file://Compute.yml --parameters file://Compute-Parameters.json --capabilities "CAPABILITY_IAM" "CAPABILITY_NAMED_IAM" -- < region >
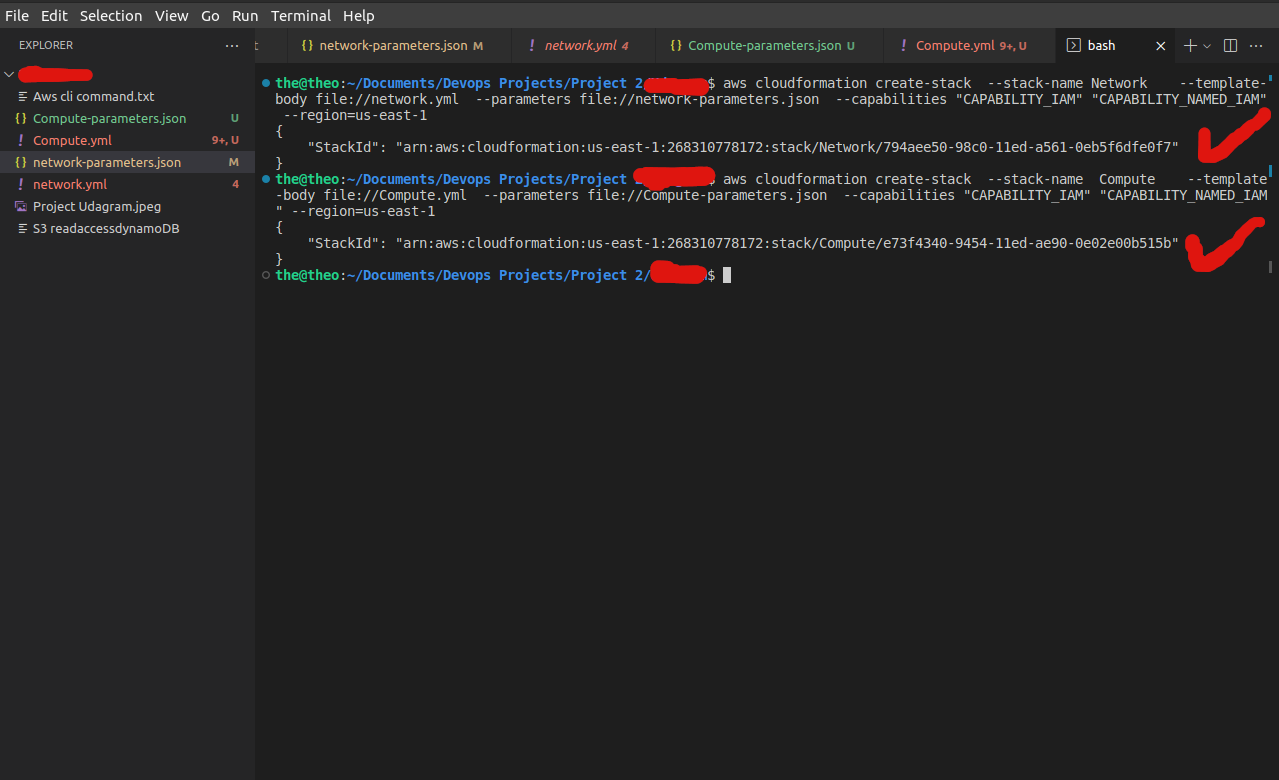
5. Lets log into the AWS management console to check our created cloud formation stack
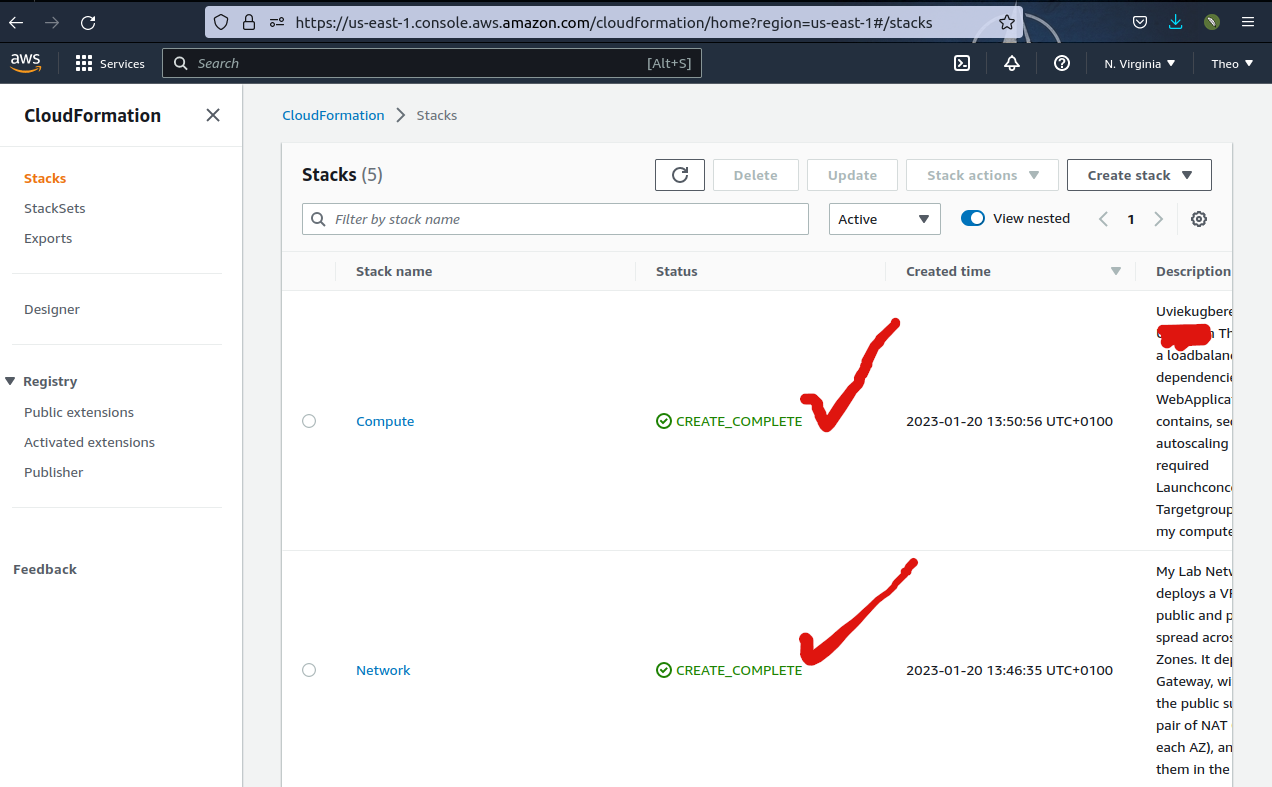
Our network and computer stacks were successfully created . Now lets look at our compute resources
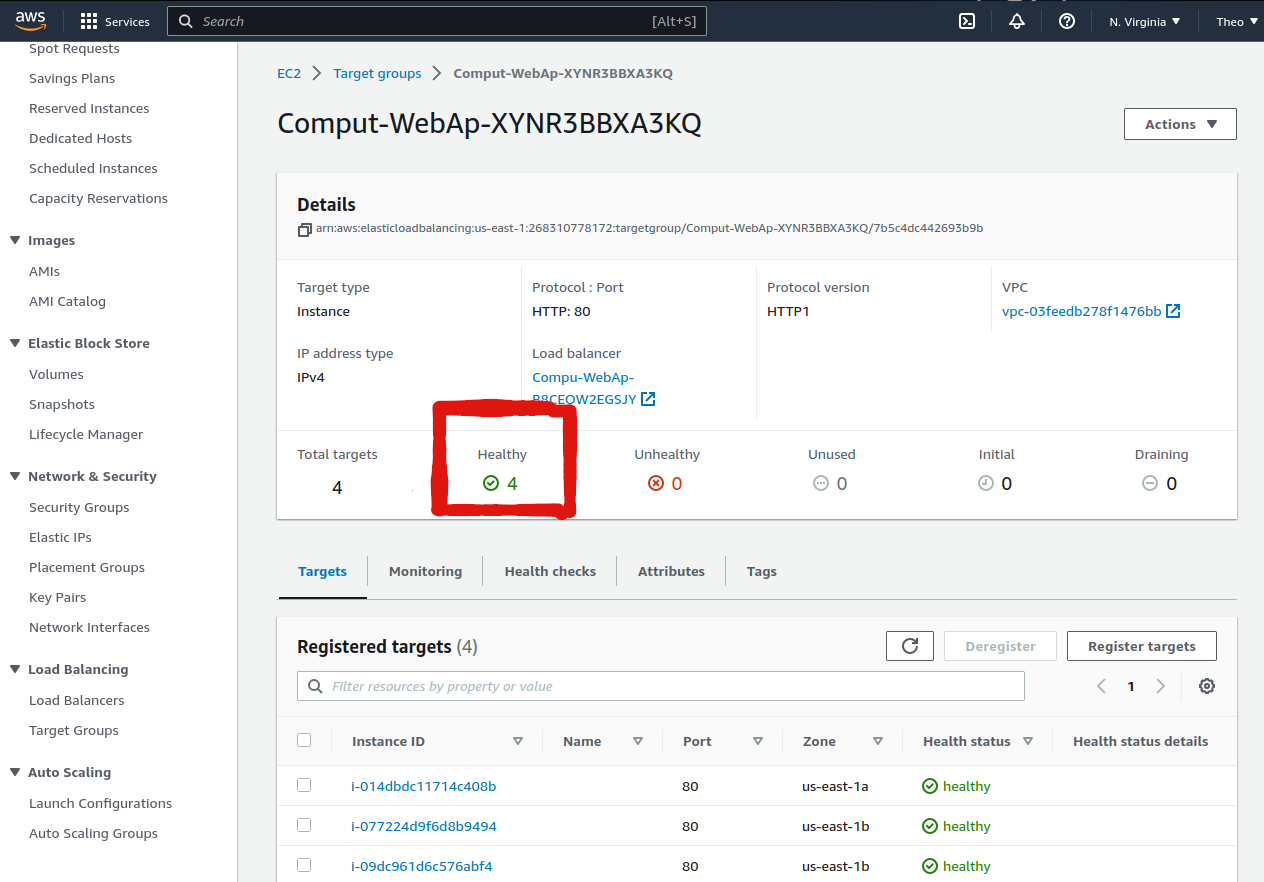
Note: The autoscaling group uses a launch template, which is typically a blueprint that describes all the settings for an instance in the Autoscaling group. It specifies the Amazon Machine Image (AMI), the instance type, the key pair, security groups, and other settings. In this project, We specified the minimum of web servers to ‘4’ and the maximum to ‘5’; hence, we see from the target group in the image above that our four default Instances are all healthy and ready to serve requests.
From the Architectural diagram of the project, we see that A load balancer sits in front of an Auto Scaling group of instances and helps to direct and distribute the incoming traffic evenly across all the instances, which helps to ensure that the instances are used efficiently and that the user experiences minimal downtime. The load balancer equally helps to protect your instances from receiving too many requests at once, which can help to prevent them from becoming overwhelmed and potentially crashing.
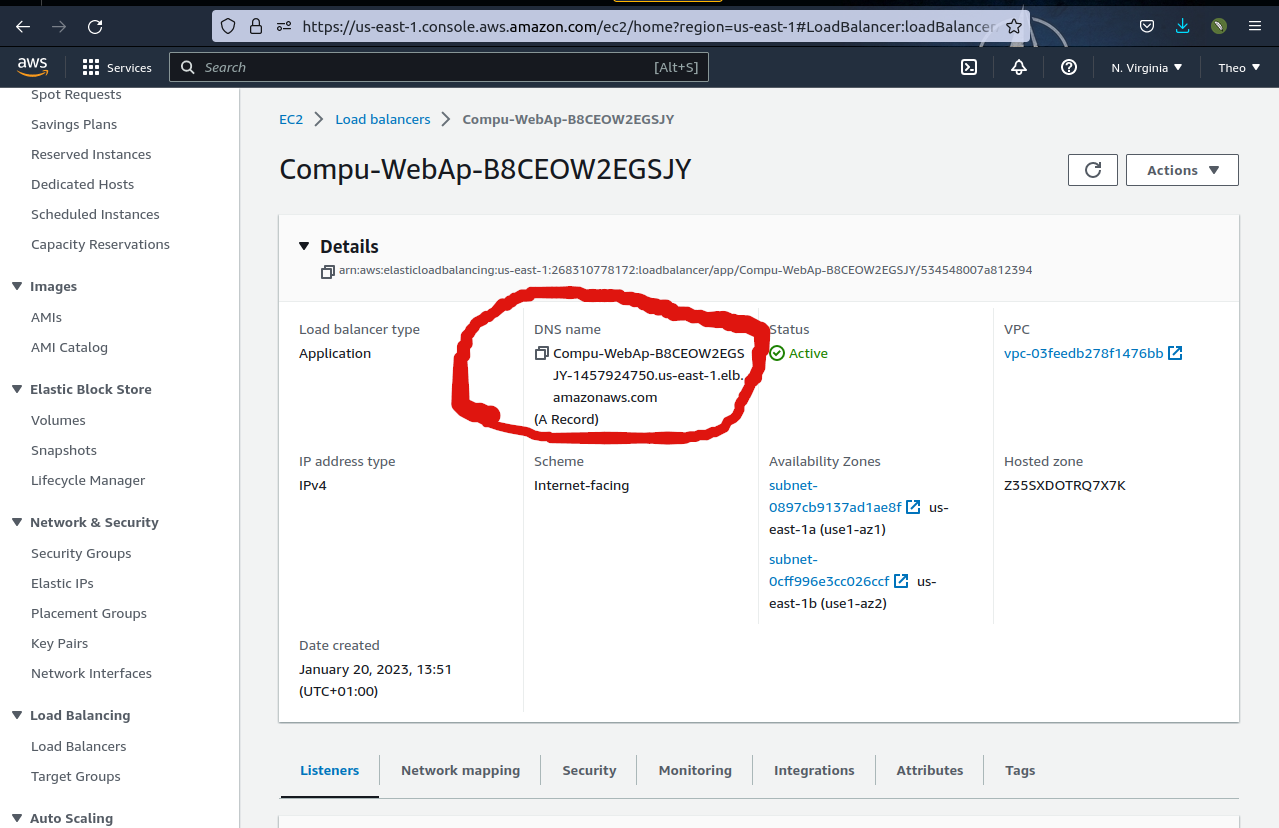
So let’s try to access the web servers by connecting to the load balancer’s public IP address or DNS hostname, which is circled in the image above
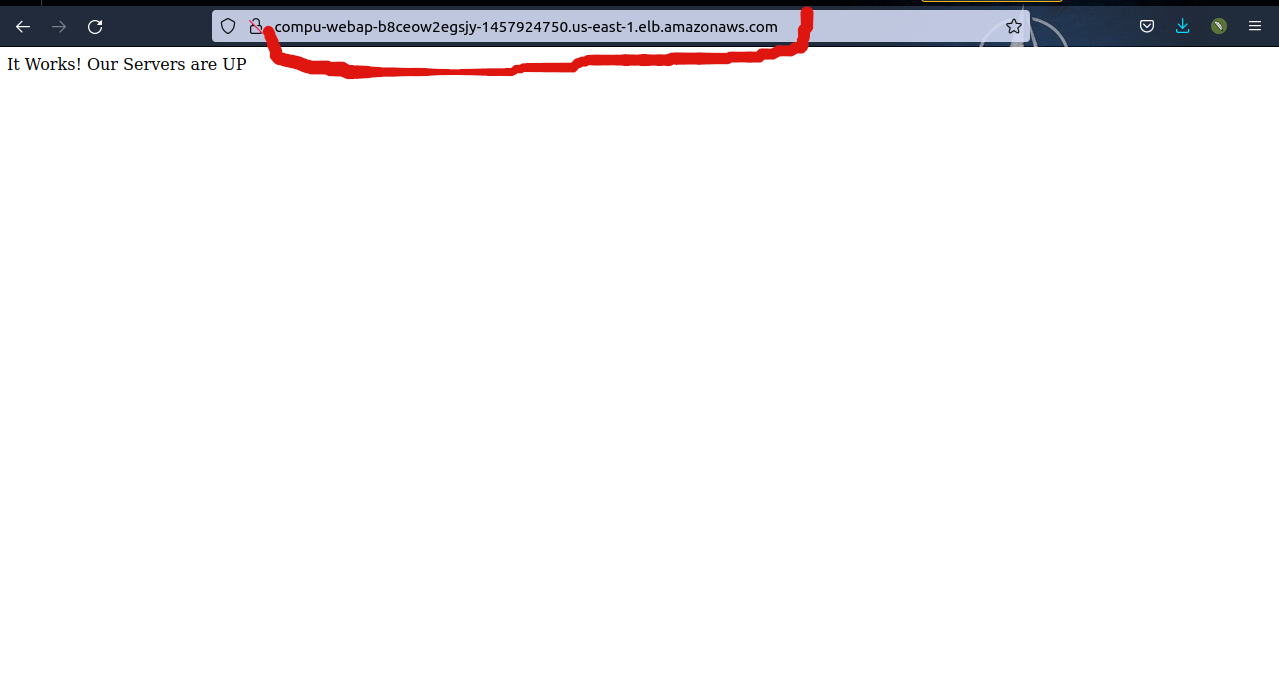
Viola!!!!!!! our servers are up and serving requests.
CONCLUSION
In conclusion, designing a fault-tolerant web application on an AWS cloud environment is crucial for ensuring that the web application is always available and reliable for users. By using services such as Amazon EC2 Auto Scaling, Elastic Load Balancing, Amazon RDS, and Amazon Route 53, you can create a highly available and fault-tolerant web application architecture that can continue to function even in the event of failures or unexpected interruptions. Additionally, deploying the web application across multiple availability zones can also help ensure that if one availability zone goes down, the application will still be available in other zones. By implementing a fault-tolerant design, businesses can minimize the risk of downtime and service interruption and ensure that their web application is able to meet the needs of its users and support the goals of the business. Using infrastructure as a code service like AWS CloudFormation can greatly simplify the process of designing a fault-tolerant web application on an AWS cloud environment by providing automation, versioning, rollback features, and collaboration capabilities. This can help to ensure that your web application is always available and reliable for users and that it can continue to function even in the event of failures or unexpected interruptions.